- Defcon Game Free Download
- Defcon Free Download
- Defcon Crack Download
- Defcon Download
- Defcon Everybody Dies Free Download
- Defcon Game Demo Download
- Defcon Linux Download
This page is a repository for the great and innovative tools that have accompanied DEF CON talks over the years. DEF CON 16 content was graciously collected and brought to you by Rob Fuller, (aka Mubix) of Room362.com If you know of a newer version of the tools or have a correction, send them to neil [at] defcon ]dot[ org.
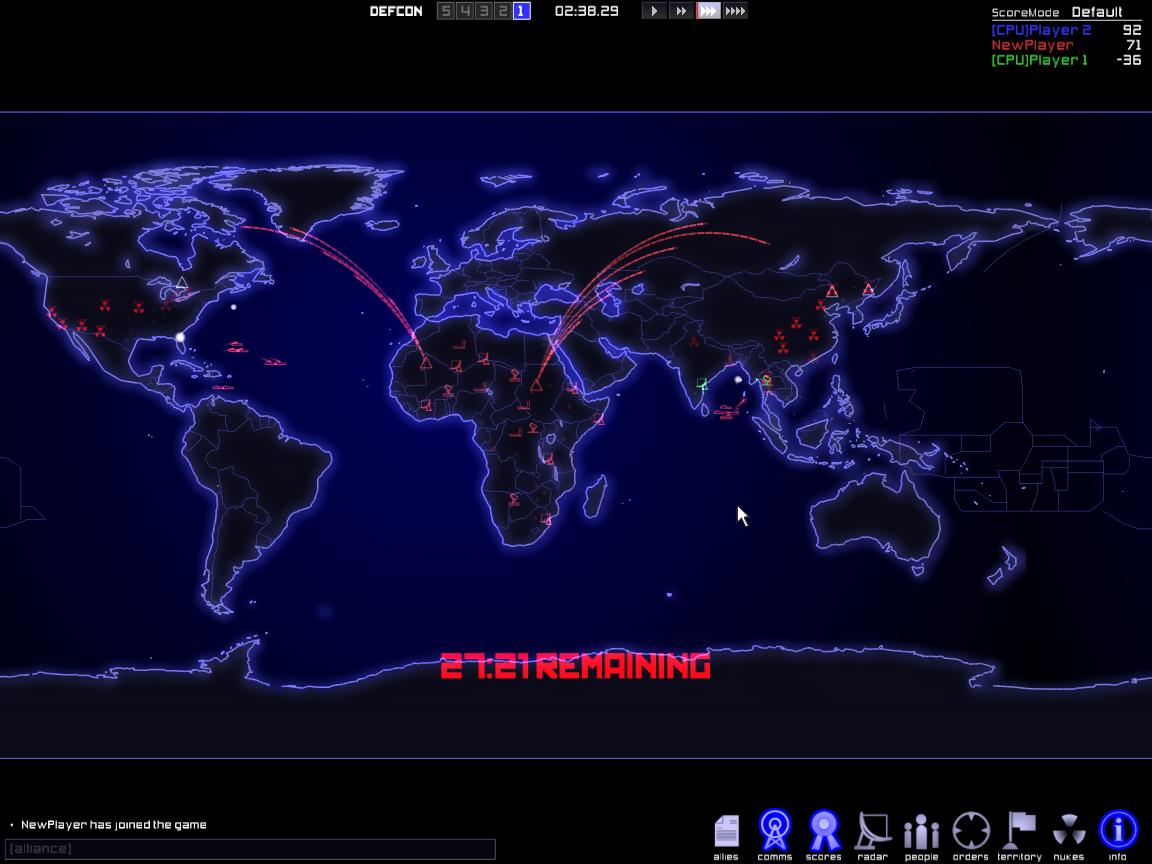
Defcon is a game about nuclear warfare. It shows how detramental a nuclear war could be. In this video I try to show you in my best ability how to play Defco. Download DEFCON for Mac to play an online multiplayer strategy simulation of global thermonuclear war.
Tools Released at DEF CON 18
gtoolbarsnoop
Download Wargames: Defcon 1. Windows XP/Vista/7/8/10. System requirements: PC compatible; Operating systems: Windows 10/Windows 8/Windows 7.
by Jeff Bryner
- Description: snoops out cookies, bookmarks, emails and favorite icon traffic from the google toolbar's network traffic.
- Homepage Link: http://jeffbryner.com/http://p0wnlabs.com
- Email Address: jeff [at] jeffbryner ]dot[ com
- Tool URL: http://p0wnlabs.com/defcon18/defcon18.zip
- Local Copy: https://media.defcon.org/DEF CON 18/DEF CON 18 tools/DEF CON 18 - gtoolbarsnoop.zip
FOCA
Informatica64
- Description FOCA is a tool for Windows Systems that allows pentester to perform a tactical fingerprinting using metadata, DNS information, search engines and public files.
- Homepage Link: http://www.informatica64.com/FOCA
- Email Address: amigosdelafoca [at] informatica64 ]dot[ com
x06d
by James Shewmaker
- Description: x06d is a Browser Enhancement Proof of Concept that defends against a variety of attacks on privacy.
- Homepage Link: http://sourceforge.net/projects/x06d/
Search Diggity
by Francis Brown and Rob Ragan
- Description: A search engine hacking tool designed to perform information gathering on multiple targets leveraging Google and Bing.
- Homepage Link: http://www.stachliu.com/index.php/resources/tools/google-hacking-diggity-project/
- Email Address: diggity [at] stachliu ]dot[ com
- Local Copy: https://media.defcon.org/DEF CON 18/DEF CON 18 tools/DEF CON 18 - searchdiggity.zip
DotNetasploit - Gray Dragon - Visual Studio xMe - Beta
by Jon McCoy
- Description: DotNetasploit is a software system that allows .NET payloads to be used against running .NET applications.
- Homepage Link: www.DigitalBodyGuard.com
- Email Address: DefCon18 [at] DigitalBodyGuard ]dot[ com
- Local Copy: https://media.defcon.org/DEF CON 18/DEF CON 18 tools/DEF CON 18 - DotNetasploitEXE.rar
FOE (Feed Over Email)
by Sho Ho
- Description: Users in Internet censored countries often find themselves unable to access foreign news websites or RSS feeds such as the ones from Voice of America, CNN, BBC, etc. Until now, the only way users in censored countries can access these websites is to use a proxy server or install a proxy software on their computer. FOE (Feed Over Email) is a new tool that allows users to receive RSS feeds from foreign websites without the need to find a working proxy server or install any proxy software. Technically, FOE is built on top of SMTP and work on most email servers as long as the user has access to POP3 and SMTP.
- Homepage Link: http://code.google.com/p/foe-project/
BlindElephant
by Patrick Thomas

- Description: The BlindElephant Web Application Fingerprinter attempts to discover the version of a (known) web application by comparing static files at known locations against precomputed hashes for versions of those files in all all available releases. The technique is fast, low-bandwidth, non-invasive, generic, and highly automatable.
- Homepage Link: http://blindelephant.sourceforge.net/
- Email: pst [at] coffeetocode ]dot[ net
Exploiting WebSphere Application Server's JSP Engine
by Ed Schaller
- Homepage Link: http://www.darkmist.net/~schallee/defcon18/
- Local Copy: https://media.defcon.org/DEF CON 18/DEF CON 18 tools/DEF CON 18 - WAS-JSP-src-1.0.0.zip
EvilGrade
Francisco Amato and Federico Kirschbaum
- Description: ISR-evilgrade: is a modular framework that allow us to take advantage of poor upgrade implementations by injecting fake updates.
- Homepage Link: http://www.infobyte.com.ar/developments.html
- Email: Francisco Amato – famato [at] infobytesec ]dot[ com, Federico Kirschbaum – fedek [at] infobytesec ]dot[ com
- Local Copy: https://media.defcon.org/DEF CON 18/DEF CON 18 tools/DEF CON 18 - isr-evilgrade-1.0.0.tar.gz
Tools from: Training the Next Generation of Hardware Hackers
by Andrew Kongs and Dr. Gerald Kane
- Description: Hardware hacking can be lots of fun but can be very intimidating getting started. Andrew Kongs and Dr. Gerald Kane wanted to spread the hardware hacking culture to others and saw incoming college engineering freshman as the perfect crowd to indoctrinate. They developed a set of hardware and software tools to help their incoming students play with low-level software and embedded systems.
After sharing the tools with their student audience, they want to share the tools they built with everyone so that those interested can get their feet wet. Want to learn more about the nitty gritty of how microcontrollers and how embedded systems tick (and how to break them) without diving in eyeballs deep? So do many people and the guys from the University of Tulsa are here to help. - Homepage Link: http://ee.base2.us/
Drivesploit
by Wayne Huang
- Description: Drive-by download testing framework for metasploit.
- Homepage Link: http://www.drivesploit.org/
- Latest Release: git://github.com/waynearmorize/drivesploit
URFUKED
by Monta Elkins
- Description: Do you check every USB plug on your computer before you log-in? Didn't think so... URFUKED is used to take over the user's keyboard input and quickly execute preprogrammed attacks with the user's privileges.
- Homepage Link: http://www.hackerwarrior.com/urfuked
Bliztableiter
by FX
- Description: A tool for securing RIA Flash Content before using it.
- Homepage Link: http://blitzableiter.recurity.com/
- Local Copy: https://media.defcon.org/DEF CON 18/DEF CON 18 tools/DEF CON 18 - Blitzableiter.rev175.binary.zip
Seccubus
by Frank Breedjik
- Description: Seccubus automates regular vulnerability scans with Nessus and OpenVAS and provides delta reporting. Seccubus effectively reduces the analysis time for subsequent scans of the same infrastructure by only reporting delta findings.
- Homepage Link: http://www.seccubus.com/
- Local Copy: https://media.defcon.org/DEF CON 18/DEF CON 18 tools/DEF CON 18 - Seccubus-1.5.2.tar.gz

Tools from: Breaking Bluetooth
by JP Dunning
- Homepage Link: www.hackfromacave.com
- SpoofTooph: http://www.hackfromacave.com/projects/spooftooph.html
- Bluetooth Profiling Project: http://www.hackfromacave.com/projects/bpp.html
- vCardBlaster: www.hackfromacave.com/vcardblaster.html
- Blueper: www.hackfromacave.com/blueper.html
- Pwntooth: www.hackfromacave.com/pwntooth.html
- Local Copy: https://media.defcon.org/DEF%20CON%2018/DEF%20CON%2018%20tools/DEF%20CON%2018%20-%20bluetooth.zip
Razorback
by Patrick Mullen and Ryan Pentney
- Description: Razorback is...
● An Open Source framework (GPLv2) to enable advanced processing of data and detection of events
● Able to get data as it traverses the network
● Able to get data after it's received by a server
● Able to perform advanced event correlation
● …Our answer to an evolving threat landscape - Homepage links: http://sourceforge.net/projects/razorbacktm, http://sourceforge.net/projects/nuggetfarm
- Local Copy: https://media.defcon.org/DEF%20CON%2018/DEF%20CON%2018%20tools/DEF%20CON%2018%20-%20razorback.zip
Tools Released at DEF CON 16
PE-Scrambler
by Nick Harbour
- Description: (pending update)
- Homepage Link: http://www.rnicrosoft.net/
- Email Address: nick.harbour [at] gmail ]dot[ com
- Local Copy: https://media.defcon.org/dc-16/tools/PEScrambler_v0_1.zip
Packet-O-Matic
by Guy Martin
- Description: 'A real time packet processor' - It extracts and can reinject packets. This includes VoIP calls in real time, Cable Modem (DOCSIS) traffic, and a whole host of others.
- Homepage Link: http://www.packet-o-matic.org/
- Email Address: gmsoft [at] tuxicoman ]dot[ be
- Local Copy: https://media.defcon.org/dc-16/tools/packet-o-matic-svn-20080814.tar.gz
SA Exploiter
by Securestate
- Description: A GUI SQL Injection tool that creates SQL injection queries and brakes the 64k barrier using MS Debugger.
- Homepage Link: http://securestate.com/pages/free-tools.aspx
- Local Copy: https://media.defcon.org/dc-16/tools/sa_exploiter.rar
Fast-Track
by Securestate
- Description: A python based tool that automates several different types of attacks including Metasploit's Autopwn and SQL Injection
- Homepage Link: http://securestate.com/pages/free-tools.aspx
- Local Copy: https://media.defcon.org/dc-16/tools/fasttrack.tgz
Beholder
by Nelson Murilo and Luis Eduardo
- Description: An open source wireless IDS program
- Homepage Link: http://www.beholderwireless.org/
- Email Address: bh [at] beholderwireless ]dot[ org
- Local Copy: https://media.defcon.org/dc-16/tools/beholder_wireless-0.8.6.tgz
BSODomizer
by Joe Grand (Kingpin) and Zoz
- Description: A gadget that interfaces between a computer and a VGA monitor and flashes a fake BSOD (Blue Screen of Death) at random time intervals or when triggered by an infrared remote control.
- Homepage Link: http://www.bsodomizer.com
- Email Address: kp [at] kingpinempire ]dot[ com
The Middler
by Jay Beale
- Description: The end-all be-all of MITM tools
- Homepage Link: http://code.google.com/p/middler/
- Alternate Link: http://www.inguardians.com/tools/
- Download Link: http://middler.googlecode.com/files/middler-1.0.tgz
ClientIPS
by Jay Beale
- Description: An open source inline 'transparent' client-side IPS
- Homepage Link: http://www.ClientIPS.org/ (Online?)
Marathon Tool
by Daniel Kachakill
- Description: A Blind SQL Injection tool based on heavy queries
- Download Link: http://www.codeplex.com/marathontool
- Email Address: dani [at] kachakil ]dot[ com
- Local Copy: https://media.defcon.org/dc-16/tools/MarathonTool.zip
Defcon Game Free Download
The Phantom Protocol
by Magnus Brading
- Description: A Tor-like protocol that fixes some of Tor's major attack vectors
- Homepage Link: http://code.google.com/p/phantom
- Email Address: brading [at] fortego ]dot[ se
ModScan
by Mark Bristow
- Description: A SCADA Modbus Network Scanner
- Homepage Link: http://modscan.googlecode.com/
- Email Address: mark.bristow [at] gmail ]dot[ com
- Local Copy: https://media.defcon.org/dc-16/tools/modscan_0.1.tar
Grendel Scan
by David Byrne
- Description: Web Application scanner that searches for logic and design flaws as well as the standard flaw seen in the wild today (SQL Injection, XSS, CSRF)
- Homepage Link: http://grendel-scan.com/
iKatinteractive Kiosk Attack Tool
by Paul Craig
(This site has an image as a banner that is definitely not safe for work! You have been warned)
- Description: A web site that is dedicated to helping you break out of Kiosk jails
- Homepage Link: http://ikat.ha.cked.net
- Email Address: paul.craig [at] security-assessment ]dot[ com
DAVIX
by Jan P. Monsch and Raffael Marty
- Description: A SLAX based Linux Distro that is geared toward data/log visualization
- Homepage Link: http://code.google.com/p/davix/
- Download Link: http://www.geekceo.com/davix/davix-0.5.0.iso.gz
- Email Addresses: jan.monsch [at] iplosion ]dot[ com and raffy [at] secviz ]dot[ org
CollabREate
by Chris Eagle and Tim Vidas
- Description: An IDA Pro plugin with a server backend that allows multiple people to collaborate on a single RE (reverse engineering) project.
- Homepage Link: http://www.idabook.com/defcon
- Email Addresses: cseagle [at] gmail ]dot[ com and tvidas [at] gmail ]dot[ com
VMware Pen-Testing Framework
by John Fitzpatrick
- Description: A collection of tools created to pen-test VMware environments
- Homepage: http://labs.mwrinfosecurity.com
- Email Address: john.fitzpatrick [at] mwrinfosecurity ]dot[ com
Dradis
by etd
- Description: A tool for organizing and sharing information during a penetration test
- Homepage: http://dradis.sourceforge.net
- Email Address: etd [at] nomejortu ]dot[ com
- Local Copy: https://media.defcon.org/dc-16/tools/dradis-v2.1.1.tar.gz & https://media.defcon.org/dc-16/tools/dradis-v2.1.1-setup.exe
Squirtle
by Kurt Grutzmacher
- Description: A rogue server with controlling desires that steals NTLM hashes.
- Homepage: http://code.google.com/p/squirtle
- Email Address: grutz [at] jingojango ]dot[ net
- Local Copy: https://media.defcon.org/dc-16/tools/squirtle-1.1a.zip
WhiteSpace
by Kolisar
- Description: A script that can hide other scripts such as CSRF and iframes in spaces and tabs
- Download Link: DEF CON 16 CD
VoIPer
by nnp
- Description: VoIP automated fuzzing tool with support for a large number of VoIP applications and protocols
- Homepage Link: http://voiper.sourceforge.net/
- Local Copy: https://media.defcon.org/dc-16/tools/voiper-0.07.tar.gz
Barrier
by Errata Security
- Description: A browser plugin that pen-tests every site that you visit.
- Homepage Link: http://www.erratasec.com
- Email Address: sales [at] erratasec ]dot[ com
Psyche
by Ponte Technologies
- Description: An advanced network flow visualization tool that is not solely based on time.
- Homepage Link: http://psyche.pontetec.com/
- Local Copy: https://media.defcon.org/dc-16/tools/psyche-0.4.tar.gz
(Updated 15 Oct 20)
*****
Defcon Free Download
Archives
PRODUCTS
COMPLETE LIST
RECENT RELEASES
- Marching Eagles -
Marengo
Waterloo
- Combat Actions -
Peleliu
Murphy's Heroes / Hurtgen Forest
Vietnam
The Days of the Dead
- DigitalGameworks -
The Drift 1879
The Alamo
Patriot Battles
Vengeance
Desperate Glory
Zulu Dawn
DEFCON-2
Monuments Men
- Tactical Studies Series -
TIGERS UNLEASHED
POINT OF ATTACK-2
- HPS Signature Sims -
AIDE DE CAMP-2
- Squad Battles -
VIETNAM
TOUR OF DUTY
THE PROUD & THE FEW
EAGLES STRIKE
KOREAN WAR
ADVANCE OF THE REICH
PACIFIC WAR
SOVIET-AFGHAN WAR
WINTER WAR
SPANISH CIVIL WAR
DIEN BIEN PHU
RED VICTORY
- Modern Campaigns -
MIDEAST '67
FULDA GAP '85
KOREA '85
NORTH GERMAN PLAIN '85
DANUBE FRONT '85
- Ancient Warfare -
PUNIC WARS
GALLIC WARS
ALEXANDRIAN WARS
GREEK WARS
ROMAN CIVIL WARS
- Modern Airpower -
WAR over VIETNAM
WAR over the MIDEAST
- Air Campaigns of WW2 -
DEFENDING THE REICH
- Naval Campaigns -
JUTLANDTSUSHIMA
GUADALCANALMIDWAY
- Panzer Campaigns -
NORMANDYSMOLENSK
KHARKOVTOBRUK '41
BULGE '44KORSUN '44
KURSK '43SICILY '43
RZHEV '42MOSCOW '41
MARKET-GARDEN '44
EL AlAMEIN '42
FRANCE '40SALERNO '43
STALINGRAD'42
MINSK '44BUDAPEST '45
SEA LION
- Total War In Europe -
FIRST BLITZKRIEG
SOUTHERN FRONT
- Napoleonic Battles -
Defcon Crack Download
NAPOLEON'S RUSSIAN CAMPAIGN
CAMPAIGN ECKMUHL
WAGRAMWATERLOO
JENA-AUERSTAEDT
AUSTERLITZ
- Early American Battles -
18121776
FRENCH & INDIAN WAR
MEXICAN WAR
- American Civil War -
CORINTHOZARK
FRANKLIN
SHILOHPENINSULA
GETTYSBURG
VICKSBURG
ATLANTACHICKAMAUGA
ANTIETAM
CHANCELLORSVILLE
- Musket & Pike -
RENAISSANCE
- First World War Campgns -
FRANCE '14
- Professional Military -
DECISIVE ACTION
FUTURE FORCE
- Maps & Publications -
Wehrmacht: Moscow 1939
Defcon Download
UPDATES/PATCHESAide De Camp (1/2)
Air Campaigns Of WWII
Ancient Warfare
Civil War Battles
Decisive Action
Digital Gamworks/JLSSG
Early American Series
Marching Eagles
Modern Air Power
Modern Campaigns
Musket & Pike
Napoleonic Battles
Naval Campaigns
Panzer Campaigns
Squad Battles
Tactical Studies Series
Total War In Europe
WWI Campaigns
HAVING PROBLEMS?
Defcon Everybody Dies Free Download
VISTA™ & WIN7 ISSUES
EARLY AMERICAN SERIES
AIDE DE CAMP (1/2)
TOP2/PANTHERS SERIES
PANZER CAMPAIGNS
GALLIC WARS
WEB SITE ADMIN
FAQ
HINTS AND TIPS
AIDE DE CAMP-2
PANZER CAMPAIGNS
DECISIVE ACTION
FREE DOWNLOADS
MAIN MENU
17761812
AIDE DE CAMP (1/2)
TOP2/PANTHERS SERIES
PANZER CAMPAIGNS
DECISIVE ACTION
OTHER
PURCHASING
BUY NOW DIRECT
GENERAL INFORMATION
PRIVACY STATEMENT
RETAILER LIST
STANDARD TERMS
PROFESSIONAL MILITARY
Defcon Game Demo Download
USAF PROJECT (POA-2)
ABOUT US
HPS STAFF
CONTACT HPS
LINKS
Defcon Linux Download
©1990-2020 HPS SimulationsThe HPS Logo and all series/game titles on this site trademark (TM) HPS Simulations. All other logos trademark of their respective owners.